| 2003 |

|
YEAR BOOK |
Letterkenny Institute of Technology & University of Ulster
|
Steganography
|
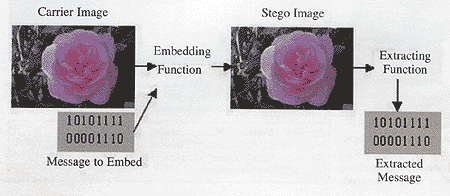
The initial aim of this study was to investigate steganography and how it is implemented. Based on this work, a number of common methods of steganography were implemented and their strengths and weaknesses were evaluated. Image based steganography was used as it is the most common form. To provide a common frame of reference, all of the steganography methods implemented and analysed used GIF images.
Seven steganographic methods were implemented. The methods were chosen for their different strengths in terms of resistance to different types of steganalysis or their ability to maximise the size of the message they could store. All of the methods used were based on the manipulation of the least significant bits of pixel values or the rearrangement of colours to create least significant bit or parity bit patterns which correspond to the message being hidden.
As all of the methods evaluated required either colour reduction of the original images palette or colour substitution in the stegoed image, they all had their own weaknesses, as the stegoed image inevitably suffered some distortion from the steganography process. In the case of colour reduction based techniques, there were strong indications of steganography in the palette as well. Overall the colour rearrangement technique appeared to be the most resistant to detection as long as suitable images were chosen. Techniques which attempt to maximise the message size they can store appear to be the least resistant to detection.
Contact: Karen Bailey, School of Science, Letterkenny Institute of Technology;
Tel: 074- 918 6311; E-mail: [email protected]